Securing the Digital Edge: Why Cybersecurity Assessments Matter More Than Ever
Preparing for an Era of Unprecedented Cyber Risk
In Brief
- Cybersecurity assessments are essential for identifying risks and ensuring business continuity in today’s digital landscape.
- Effective assessments enable strategic resource allocation and strengthen regulatory compliance.
- Regular security evaluations help organizations build resilience against evolving cyber threats while maintaining stakeholder trust.
The Urgency of Cybersecurity
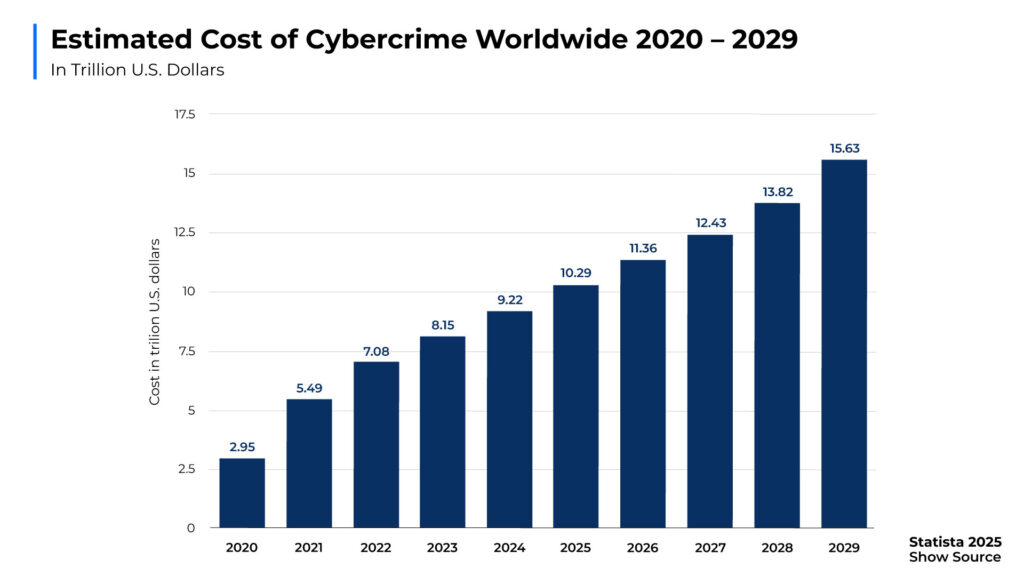
The pace of digital transformation has never been faster, unlocking new opportunities for innovation and growth. Yet, this rapid evolution comes with significant risks. Cybercrime is projected to cost businesses $15.63 trillion annually by 2029, underscoring the financial magnitude of the threat landscape. In 2025 alone, global cyberattacks surged by over 105% compared to 2020, demonstrating the growing scale and sophistication of these challenges.
In today’s hyper-connected world, the question isn’t whether your organization will face a cyberattack—it’s when. Effective cybersecurity is no longer a reactive measure; it’s a strategic pillar for business continuity and trust. At the core of any robust cybersecurity strategy lies a comprehensive cybersecurity assessment, a process that aligns security practices with operational goals, mitigates risk, and ensures resilience.
Why is Cybersecurity Assessment Important?
- Strategic Resource Allocation: Conducting effective cybersecurity assessments allows organizations to identify their most critical assets and vulnerabilities. This enables them to prioritize resources toward areas requiring the most attention. Such a targeted approach ensures that investments yield maximum security benefits while minimizing potential losses. Regular assessments provide data-driven insights, empowering organizations to make strategic decisions and adapt their resource allocation strategies to address emerging threats effectively.
- Enhancing Regulatory Compliance: Many industries operate under strict regulations regarding data protection and cybersecurity. Regular assessments help organizations stay informed about these requirements and ensure the necessary controls are implemented to achieve compliance. Detailed documentation of security practices is crucial during audits, demonstrating adherence to regulations and helping organizations avoid fines or legal consequences. Furthermore, ongoing assessments help organizations identify gaps in compliance, stay ahead of evolving regulations, and implement recommended improvements to maintain robust security standards.
Navigating Modern Risks: The Evolving Cyber Threat Landscape
The cybersecurity challenges of 2025 represent a dramatic escalation in complexity and scale. In a connected digital world shaped by increasingly organized threat actors and a rapidly expanding ecosystem, organizations face unprecedented risks. Addressing these challenges requires a clear understanding of emerging vulnerabilities and a proactive approach to mitigating them.
- Emerging Threat Vectors
- Advanced AI-Driven Attacks: Artificial intelligence (AI) has revolutionized the cybercrime landscape, enabling threat actors to deploy sophisticated, automated attacks with unprecedented precision. These AI-powered threats can adapt to defensive measures and execute highly personalized social engineering campaigns, presenting a formidable challenge to traditional security approaches.
- Persistent Challenges
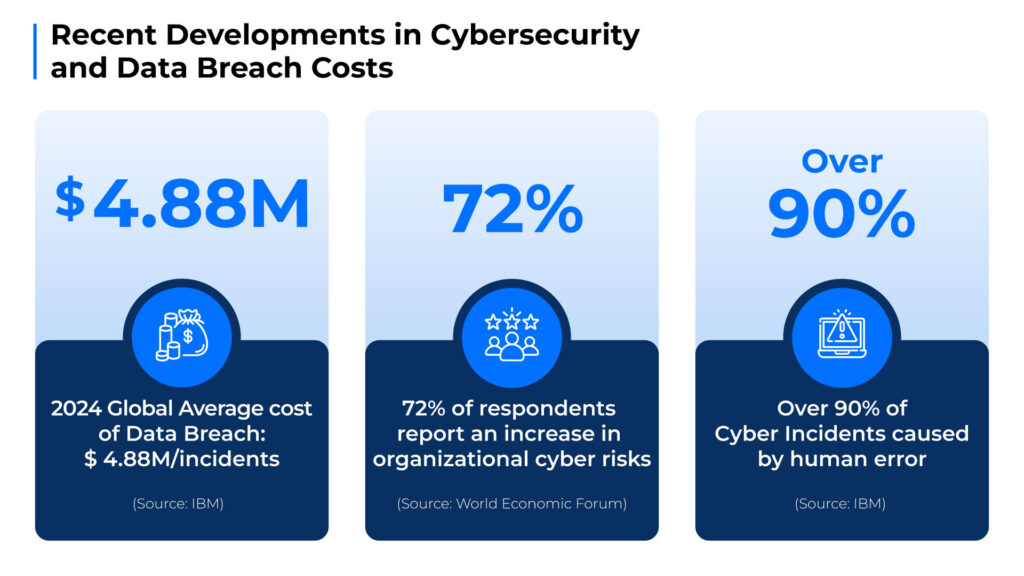
- Human Factor: Despite technological advances, human error remains a critical vulnerability, contributing to over 90% of cyber incidents. Social engineering attacks continue to exploit gaps in awareness and training, highlighting the necessity of comprehensive security education programs, and creating a cybersecurity culture
- Ransomware Evolution: Modern ransomware attacks have evolved beyond mere data encryption to target critical operational systems. The proliferation of ransomware-as-a-service platforms has democratized cybercrime, enabling less sophisticated actors to launch devastating attacks.
Strategic Framework for Cybersecurity Excellence
Assessment Fundamentals: Building Blocks of Security
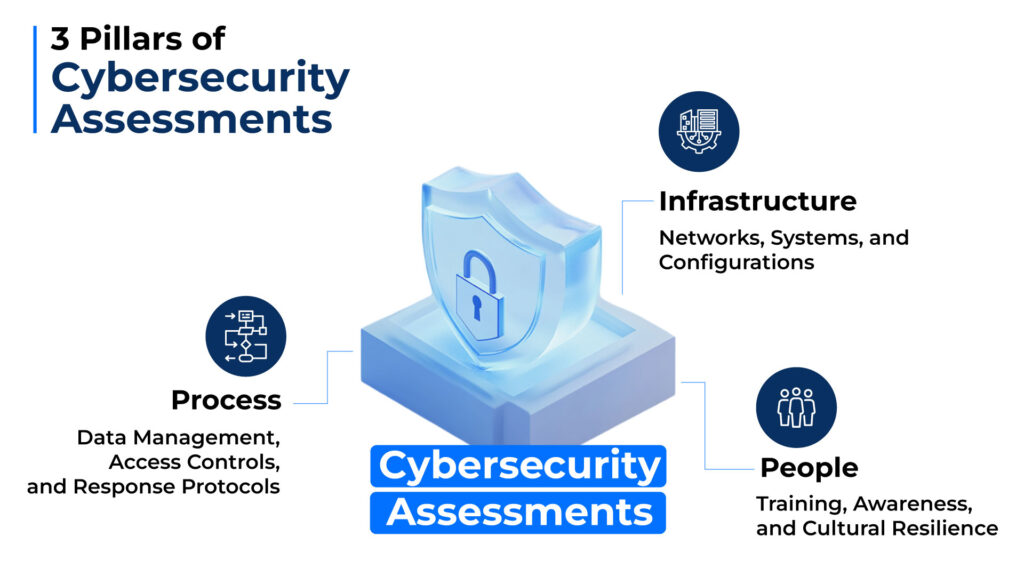
Comprehensive cybersecurity assessments are essential to identifying and addressing vulnerabilities across three key dimensions:
- Infrastructure: Analyze networks, system configurations, and technology ecosystems to identify technical vulnerabilities.
- Processes: Evaluate data management, access controls, and incident response protocols.
- People: Assess organizational awareness and resilience against social engineering threats.
Prioritizing Resources Strategically
With finite resources, organizations must allocate investments where they matter most:
- Risk Categorization: Identify and prioritize high-impact threats.
- Cost-Benefit Analysis: Balance security investments against potential losses.
- Performance Tracking: Measure the effectiveness of cybersecurity initiatives over time.
Aligning with Regulatory Standards
Compliance with evolving regulations is non-negotiable in today’s global economy:
- PDPA: Personal Data Protection Act
- GDPR: Protecting personal data and privacy rights.
- ISO 27001: Demonstrating leadership in information security management.
Embedding Incident Preparedness
Modern organizations need to be ready not just to prevent attacks but also to respond swiftly and effectively:
- Detection and containment protocols.
- Business continuity and disaster recovery strategies.
- Stakeholder communication and post-incident improvement plans.
Empowering Your Cybersecurity Strategy with Expert Solutions
Comprehensive Security Solutions
We combine innovative technology with deep industry expertise to deliver:
- Advanced threat detection and response systems.
- Proactive monitoring and tailored security training.
- Regular assessments and penetration testing for continuous improvement.
Tailored Expertise Across Industries
Our solutions address the unique challenges of sectors such as:
- Financial Services: Compliance and fraud prevention.
- Healthcare: Patient data protection.
- Manufacturing: Supply chain resilience.
- Retail: Securing payment ecosystems.
Securing Tomorrow’s Digital Economy with Bluebik Titans
In a world where cyber risks are escalating at an unprecedented pace, resilience is not optional—it’s essential. By investing in regular cybersecurity assessments and adopting a proactive security strategy, organizations can not only safeguard their assets but also create a foundation for sustained trust and growth.
Contact Bluebik Titans today to start securing your digital future!
✉ [email protected]
☎ 02-636-7011









![Thumbnail [Post Event] HOW](https://bluebik.com/wp-content/uploads/2025/12/Thumbnail-Post-Event-HOW.png)