Blubik shares its clear vision of 3 important cybersecurity issues in 2023 when businesses should have ‘cyber resilience’ to cope with the cyberattacks that will cause damage worth US$8 trillion
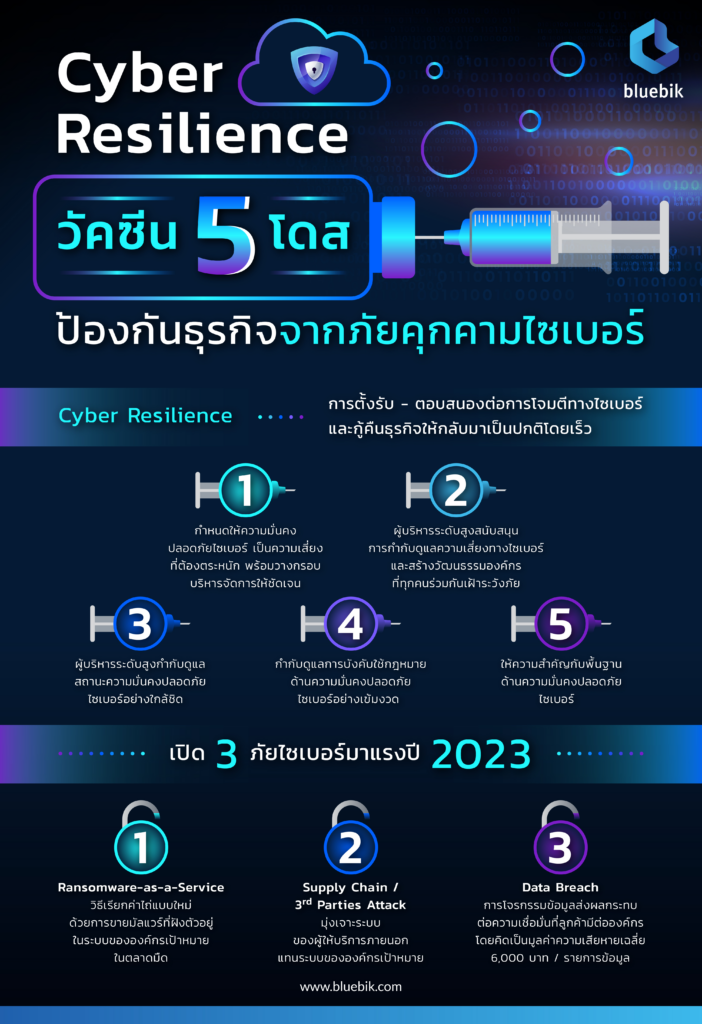
Bluebik Group Public Company Limited (BBIK), a leading consultancy on end-to-end digital transformation, presents trends and perspectives on cybersecurity in 2023. It points to the three dire cyber threats that will challenge businesses. They are rapidly spreading ransomware-as-a-service, the supply chain attacks that will be around the corner, and the data breach that will affect clients’ confidence in organizations. Businesses should, therefore, quickly eliminate the risks with “cyber resilience”. Its five elements will enable organizations to effectively protect themselves from cyberattacks, fight back and restore their business.
Pochara Arayakarnkul, Chief Executive Officer of Bluebik Public Company Limited, said digital transformation has been of critical importance to the business sector for years because the application of technologies such as cloud computing, blockchain, artificial intelligence (AI) and the Internet of Things (IoT) creates competitive edge and opportunities for business growth. However, they make business ecosystems complex and full of the loopholes or weak points which cybercriminals can exploit. The more technologies are needed, the more cyber threats there are. Thus, cybersecurity becomes a serious concern of leaders at worldwide organizations.
Damage caused by cyber threats is growing. The World Economic Forum expects damage from cyberattacks will reach US$8 trillion in 2023, rising by 15% year-on-year. Increase will also happen to expenses on cybersecurity that will go up by 12% from spending in 2022 to US$194 billion. The soaring threats indicate that it is time for organizations to strengthen their cybersecurity.
Regarding the sector most vulnerable to cyberattacks, Bluebik looks at professional service providers, followed by financial organizations, health businesses, hospitals, retail and hotels. The 3 greatest cyber threats in detail are as follows.
1) Ransomware – It will spread faster and grow in number because of ransomware-as-a-service. Malware will be released and penetrate into important systems for ransom.
A new chapter of ransomware began when hackers developed ransomware-as-a-service which replaces conventional ransomware. In black markets, hackers sell malware already installed in target systems on the condition that buyers will share collected ransoms with them. Consequently, from now on ransom demands via malware will be made easier and faster because those who hold systems for ransoms do not have to be experts. All they need is only access to a black market or an online community of hackers.
According to cybersecurity units in America, cyber ransoms averaged out US$250,000 in the third quarter of this year and about 58% of organizations fell victim to ransomware. Of them, 14% had to pay ransom more than once and their majority took longer than a month to repair their damage.
2) Supply chain/third party attacks will be around the corner: It may be more difficult to attack target organizations because they have bolstered their defense. Hackers then change their strategies. They turn to attack the systems of the vendors who offer services to many organizations and have access to the back-office systems of their corporate clients. Hackers use the breached systems of vendors to penetrate the systems of their target organizations. Supply chain attacks will increase significantly, according to Bluebik Titans.
A survey by Ponemon Institute found that over the past year, 54% of polled organizations suffered from cyberattacks through supply chains and vendors. Only 34% believed that they would receive warnings from their vendors whose systems were attacked. As much as 60% of the surveyed organizations feared that supply chain attacks would grow.
3) Data breach may result in the unexpectedly great loss of reputations, confidence and money – Data breach is frequent in cyberspace and money is its prime goal. Targets are important data such as classified data on trade and intellectual properties and the personal data of customers which will be held for ransom or sold in black markets. Damage from data breach average out at about 6,000 baht per record. Data breach damages attacked organizations in many ways including their costs of solutions, stalled business and loss of customers’ confidence which is the greatest damage.
IBM estimated that in 2022 damage from data breach at organizations in Southeast Asia would be as high as US$2.87 million per incident. It found that 83% of surveyed organizations experienced more than one incident of data breach and 45% of attacked organizations suffered from data breach via cloud computing which is increasingly used by organizations that may still lack effective security systems.
Polnsutee Thanesniratsai, Director of Bluebik Titans Company Limited, said all organizations had to quickly prepare themselves to cope because cyberattacks could happen anytime and be enormously costly in terms of organizations’ finances and credibility. To be immune to cyber threats, organizations can apply the “cyber resilience” concept which consists of the five following practices.
1) Manage cybersecurity as an enterprise risk – Organizations should include cybersecurity in their risk management. Cybersecurity issues and related impacts including financial damage, the violation of laws and the dented confidence of clients and trading partners should be considered as the risks of organizations. With this mindset, executives of organizations will have frameworks for their decisions and can choose the control measures that better suit the degrees of their risks. Organizations can copy the practices of credible organizations or study them to improve their own operations.
2) Executives play key roles in governance and fostering a culture of cybersecurity vigilance – The management of cyber threats should receive support from high-level executives. They should supervise relevant policies and strategic plans, keep risks at the tolerable levels of their organizations, emphasize the importance of cyber threat surveillance and encourage everyone to take part in cyber threat vigilance and prevention. Action toward the purposes should comprise four programs – 1) a business continuity program, 2) an IT salvage program, 3) a crisis management program related to cyber threats, which covers methods to communicate with stakeholders and the selection of specialists and 4) a program to build public awareness of cyber threats, promote safe work and organize simulation exercises to make all parties better understand their roles and responsibilities.
3) High-level executives should oversee cybersecurity posture closely – High-level executives should supervise cybersecurity closely by reviewing action reports which may include major risks, management solutions, an overview of cybersecurity and a strategic plan for standard improvement.
4) Maintain compliance with cybersecurity laws and regulations – Organizations should comply with laws concerning cybersecurity and personal data protection, monitor the compliance and follow up new laws closely. Organizations can base the improvement of their cybersecurity on such laws and regulations.
5) Implement essential cybersecurity hygiene – To strengthen defense against cyber threats, organizations need resources and cooperation from all stakeholders. To some organizations, this matter is challenging and time-consuming. Cyber threats can happen anytime and damage business. Organizations should at least stick to basics such as the accurate and complete registration of information assets, multi-factor authentication, information security, system updates to close loopholes, data management, breach response plans and the management of vendor-related risks.
“Cybersecurity management is not easy. However, it is not difficult if there are expertise, management experiences and abilities to include risk management in the plans and strategies of organizations. This will result in the proper improvement of cybersecurity and internal units at organizations can operate confidently as planned and have credibility for all stakeholders inside and outside their organizations,” Mr. Polnsutee concluded.




